Like the iPhone XR before it, the iPhone 11 is the default iPhone. It's priced where flagship phones used to be priced, and it offers almost all the same features as the expensive iPhone 11 Pro models that also launched this year.
Apple's iPhone lineup today is stacked with great phones at varying price points, though. So where does the iPhone 11 fit in?That's what we'll be looking to answer in this review. And we're dubbing this a mini-review because we recently published an in-depth article on the iPhone 11 Pro and 11 Pro Max, and last year we published a full review of the iPhone XR. This year's changes from the iPhone XR to the iPhone 11 are quite modest, so today we'll focus on how this phone is different from this year's flagships and its direct predecessor.
As always, let's start with the specs.
Table of Contents
- Specifications
- Design
- Camera
- Software
- Performance
- Battery life
- The most popular iPhone
- The Good
- The Bad
- The Ugly
Specifications
The iPhone 11 measures 5.94 x 2.98 x 0.33 inches (150.9 x 75.7 x 8.4mm), and has a 6.1-inch (154.9mm) LCD display with a resolution of 1,792 x 828, a typical contrast ratio of 1,400:1, and a maximum brightness of 625 nits. The phone comes in 64GB, 128GB, and 256GB storage configurations at $699, $749, and $849, respectively.
Apple has included its A13 system-on-a-chip, which includes numerous components: a central processing unit, a graphics processing unit, an image signal processor, the Neural Engine for machine learning, and a bunch more. Apple claims that almost all aspects of the A13 are 20% faster than what we saw in the A12 that appeared in last year's iPhone XR.
Apple iPhone 11
On the wireless front, we've got a claim of gigabit LTE, plus Wi-Fi 6 and Bluetooth 5.0. The iPhone 11 also has the U1 chip we discussed in our iPhone 11 Pro review; this chip makes the phone location-aware in relation to other wireless devices nearby. Right now, the only feature that taps this is the ability to AirDrop files to another recent iPhone by physically orienting your iPhone 11 toward the target device. But there will likely be more uses for this chip in the future.
Apple has introduced spatial audio for the iPhone this year. It provides a fuller, deeper sound field than before, with Dolby Atmos support. You'll still probably want to use headphones, but it's a huge improvement over the XR's sound system.
We'll go over camera specs in the camera section of the review, since photography is a key focus of this update—in fact, the camera system is one of the only things that's substantially different from the iPhone XR we reviewed last year.
Design
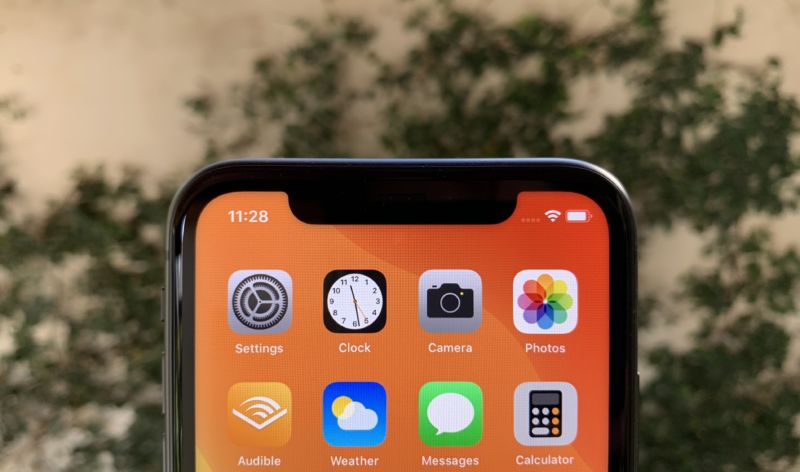
Everything about the iPhone 11 looks identical to the iPhone XR except for two things: the camera system on the back, and new color options.
Colors include red, yellow, black, white, purple, and green—many of which have an almost '90s-throwback light shade to them. Our review unit is the classic black. Like the XR, the iPhone 11 has a glossy glass back that loves to attract fingerprints as quickly and as prolifically as possible. The iPhone 11 Pro phones that we reviewed earlier this week have a new, matte finish for the back that is a little less prone to that problem—though they are still made of glass.
-
The iPhone 11.Samuel Axon
-
The back of the phone still has a glossy glass appearance, like its predecessor.Samuel Axon
-
It still has a Lightning port.Samuel Axon
-
The volume control side is the same...Samuel Axon
-
...as is the SIM tray side.Samuel Axon
-
The top remains featureless.Samuel Axon
-
The odd-looking camera system on the back.Samuel Axon
-
From left to right: iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max.Samuel Axon
-
Another view of the three phones side-by-side (same arrangement).Samuel Axon
Apple says the iPhone 11's glass back is more durable than what we got in last year's phones. But it's still glass, even if that glass is particularly strong, and damage from a drop onto a hard surface like concrete remains a risk. These phones are nigh-impossible for a user to repair should a break like that occur, and because of the way they're made, repairs from an Apple-certified repair shop or the Apple Store involve replacing huge portions of the phone to fix some pretty basic things. So you're looking at high repair costs if you don't also spring for AppleCare+.
The iPhone 11 also sports water resistance at up to two meters of depth for up to 30 minutes, another improvement over the XR.
The camera on the back has a completely new look. Whereas the iPhone XR had one camera, this one has two: a wide-angle (returning) and an ultra-wide-angle (new). The two lenses are aligned vertically and placed inside of a large-ish, rounded square of glass protruding from the back of the phone ever-so-slightly. Apple is keen to point out that both the camera bump and the rest of the back are "precision-milled from a single sheet of glass," and the glass does look handsome when you're up close.
That said, I personally feel the camera bump itself looks weird on the iPhone 11—moreso than in the Pro models. I think it's because the two lenses only occupy half of the square-shaped bump, and while there are a couple other components on the other side (like the flash), it looks lopsided and seems like it might not have been necessary have this entire square in place. Something more like what we saw with the two-camera systems in the iPhone X and XS phones would have looked a little more graceful.I also feel that the iPhone XR is just kind of bulky. It's not a very elegant-looking device; it's price over form here, with a lot of tiny compromises to bring the costs down but actually add up in terms of aesthetic experience. Of course, that sort of thing is subjective, and it's also not really that important in the grand scheme.
Other than these notes, the iPhone 11 looks identical to the iPhone XR, the design of which we talked about at length in our review last year.
Camera
The biggest changes the iPhone 11 introduces over the iPhone XR are in the various cameras on the device. On the back, we have two 12-megapixel cameras, up from one in the XR. The 12MP, wide-angle lens with a ƒ/1.8 aperture returns, but it's joined by a 12MP, ƒ/2.4 aperture ultra-wide-angle lens with a 120° field of view. This allows taking photos show much more in cramped spaces—or just in any space, really—than the wide-angle lens allowed. We'll take a look at that more closely momentarily.
A new video feature called QuickTake lets you take a short video simply by holding your finger down on the shutter button to start recording, then letting go to stop. And Apple has made big improvements to the front-facing camera. It's gone from 7MP to 12MP and supports 4K video at up to 60 frames per second (up from 1080p). It also supports slow-motion video (previously only supported on the rear cameras), so you can take "slofies" at 1080p and 240fps.
The story here is that, at this lower-than-flagship price point (although this price point used to be a flagship price point before the sticker prices started going up over the past couple of years, but I digress), many Android options offered better camera systems than the XR offered. Apple is closing the gap here with improvements in both software and hardware.
For example, the Google Pixel 3 offered a feature called Night Sight that enhanced images taken in low-light situations to be much more readable. The feature also removed noise and brightened things up while maintaining or even introducing attractive-looking contrast. Apple has answered that here with Night Mode, which does the same thing. Night Mode uses the wide-angle lens and requires you to hold the phone still for a period of time (you can define how long for different results), then produces a low-light image that doesn't look as terrible as smartphone camera low-light images historically have.
Here's an example take on the iPhone 11.
-
Taken without Night Mode on the iPhone 11.Samuel Axon
-
Taken with Night Mode on the iPhone 11.Samuel Axon
The new ultra-wide camera allows you to zoom out to 0.5x, from the usual 1x of the traditional wide-angle lens. This means you can capture more of a scene; you toggle between the two lenses by simply tapping a button in the Camera app. The transition uses some crazy machine-learning-driven techniques to make the transitions seamless and help you get a sense of which lens to use when, and it's pretty snazzy.
Here's what the difference looks like between the two zoom levels:
-
0.5x zoom on the iPhone 11, using the new ultra-wide-angle lens.Samuel Axon
-
1x zoom on the iPhone 11, using the returning wide-angle lens.Samuel Axon
You shouldn't expect a huge difference in normal photos taken with the normal wide-angle camera compared to either last year's iPhone XR or this year's iPhone 11 Pro. We didn't have an XR on hand to test, but as you can see in the photos below, it's impossible to distinguish between the regular photos taken with the 11 and those taken with the 11 Pro. However, Apple has improved on Smart HDR this year, a computational photography feature that helps bring out contrast and colors in photos. The previous implementation sometimes did unreal-looking things with human faces, and Apple has improved on that in this iteration.
-
Taken on the iPhone 11.Samuel Axon
-
Taken on the iPhone 11 Pro.Samuel Axon
-
Taken on the iPhone 11.Samuel Axon
-
Taken on the iPhone 11 Pro.Samuel Axon
-
Taken on the iPhone 11.Samuel Axon
-
Taken on the iPhone 11 Pro.Samuel Axon
Since the iPhone XR only had one camera, it had to rely on a software solution to produce some of the Portrait Lighting effects that were introduced in 2017. I'm not a fan of Portrait Lighting even on the high-end phones, and I didn't think it looked good on the XR. With this second camera, Apple seems able to get some depth information, because Portrait Lighting has improved.
It's still not a very attractive feature, though, as the images are often full of odd errors around things like hair or glasses. Apple has nonetheless added Key Light Mono, a new Portrait Lighting effect that puts a white background behind the target in a monochromatic photo.
And everything I said in the iPhone 11 Pro review about the upsides and downsides of this machine learning and ISP-driven photography stands for the iPhone 11, too.
The A13 and its components, along with Apple's software, are making a lot of decisions for you about how the image should look by default. The results are striking, and smartphone photos look better than they ever had before because of these techniques. But if you're looking to take a nice, clean image without any computational magic going on, you're generally going to be out of luck.
I don't think most people will care, though. That criticism mattered more for the iPhones Apple called "Pro." In this case, it fits the product: these features allow non-photographers to use a device that is not a professional-quality camera to take photos that most of the time look better than amateurs have been able to achieve before.
It's not unique to Apple's phones—Google and its OEMs are doing similarly impressive work over on the Android side—but that doesn't matter. If you're buying a flagship-or-close-to-it smartphone today, there's some cool photography stuff going on for amateur picture-takers.

Software
The iPhone XR ships with iOS 13 (possibly iOS 13.1 by now), Apple's latest mobile operating system. We wrote an extensive, detailed review of iOS 13 that you should check out if you want to learn about all the new features and how the system compares to alternatives.
The short version, though, is that iOS 13 remains one of the most elegantly designed operating systems in the industry, and that—along with an extremely robust app and game ecosystem—is one of the main reasons consumers buy iPhones. iOS 13 introduced a number of new features for power users, such as deeper file management and improved text editing. It also shipped with a number of bugs—so far, no common issues are major, but the polish isn't quite there.iOS 13.1 was released shortly afterwards, and it addressed many but not all of the bugs. Still, we expect this annual update cycle of iOS to be a strong one as the small stuff gets worked out.
iOS is rivaled in the marketplace by Google's Android operating system, which offers users more control and customization in some areas. Android's app ecosystem has fewer restrictions on which apps may be distributed, and it has more powerful AI features, among other things. On the other hand, iOS offers much more robust longterm device support, a greater emphasis on user privacy, well-thought-out accessibility features, and other advantages. Both mobile platforms are strong in their own ways; the choice between them comes down to personal priorities and naturally won't be the same for every person.Performance
As noted in the review for the iPhone 11 Pro, which has the same silicon, huge performance improvements aren't at the center of this update, and they don't need to be: last year's iPhones were already outperforming all the competition in the majority of benchmarks and use cases. But the A13 does knock things up a notch.
-
Samuel Axon
-
Samuel Axon
-
Samuel Axon
-
Samuel Axon
-
Samuel Axon
-
Samuel Axon
-
Samuel Axon
-
Samuel Axon
-
Samuel Axon
CPU performance is up around 15% in most tests, while the GPU saw bigger gains. This is a great phone to play games on or to try AR experiences with, there's no question about that.
Battery life
The iPhone XR already had the best battery life of any iPhone to date, so it's not surprising that the iPhone 11 doesn't claim to improve over its predecessor as much as the iPhone 11 Pro did over the iPhone XS. We didn't have an XR to test at this time, but we compared it against the iPhone 11 Pro, 11 Pro Max, and XS in our WebGL browser test, and it sits in relation to those about as much as promised and expected.
-
Samuel Axon
-
Samuel Axon
The iPhone 11 is capable of fast-charging from the right power adapters, but unfortunately, it doesn't come with one. It still comes with the 5W adapter that has been standard in iPhones for ages. That's a shame—that charger isn't enough for a battery with this capacity. It's going to take an awfully long time to charge this phone. The new iPhone 11 Pro models come with more efficient chargers, and it's disappointing that those chargers didn't come to this phone as well. Having an adequate charger seems to me like it should be a basic standard, not a premium benefit.
The most popular iPhone
Apple CEO Tim Cook has said that the iPhone XR was Apple's most popular iPhone last year, and I expect that baton to be passed to the iPhone 11 this year.
Now seems like as good a time as any to note that Apple's iPhone lineup is looking more appealing than it has for the past couple of years. That's because there are four strong choices—the iPhone 8, the iPhone XR, the iPhone 11, and the iPhone 11 Pro—at price points across a range of a thousand dollars, all the way from $449 to $1449. Starting at $699 (though that's for 64GB, which is not going to be enough for everyone), the iPhone 11 arguably sits at the sweet spot.
It improves on the slightly cheaper iPhone XR in noteworthy ways. Yet the only major downsides for this phone as compared to the much, much more expensive iPhone 11 Pro models are a markedly inferior screen, a slightly bulkier and less flashy design, and the lack of a telephoto camera lens. (It also doesn't get some LTE speed increases that Apple brought to the Pro models.) That might sound like a long list, but none of them is going to be particularly consequential for most people.
If you're considering upgrading from an iPhone 7 or earlier, the iPhone 11 is a dramatic step up in every respect, provided you don't mind having a much larger phone. If you want a smaller phone, the iPhone 8 is still an attractive buy for those who are coming from older phones, though it lacks many of the nifty new features introduced in the X-series phones. And if you want all the bells and whistles of Apple's iPhone X-derived modern lineup, but camera features aren't as important to you, the iPhone XR is also an option at a lower price than the iPhone 11.
I still think Apple needs an SE-like one-handed phone with modern tech in its lineup, and I'd like to see the company offer a version of the iPhone that does not have the disaster-prone glass back. But those omissions aside, iPhone buyers have more choices than they have in a while. And amidst that, I think this is the phone the majority of consumers are going to buy. Yes, the iPhone 11 Pro is outstanding. But it's too expensive for the majority of consumers.
If you're looking to live in Apple's mobile ecosystem, but you don't care about bleeding-edge OLED displays or attention-grabbing designs and premium materials, this is the way to go. Like the iPhone XR last year, we're giving it the Ars Approved badge and recommending it as the iPhone to buy for most people. Just be ready to spend a little more than the price of the phone on extras like AppleCare+, protective cases, or AirPods if you want the best experience.
The Good
- It's a little cheaper than last year's XR, but it offers all the same features and more
- The new ultra-wide-angle camera is both impressive and useful
- It has the same performance as Apple's flagships this year—far better than any Android phone at this price point
- iOS 13 is a strong mobile operating system with a vibrant app and game ecosystem
- Improves on the battery life of last year's longest-lasting iPhone
- A greater emphasis on user privacy and security than most competing phones
The Bad
- It's made of fragile glass and can generally only be repaired by Apple at great expense (unless you buy AppleCare+)
- Its design is bulky and a little inelegant, with an odd-looking camera system
- The cheap price is undermined by the fact that you might want to consider AppleCare+—and wireless headphones, if you don't already have them
- LTE speeds lag well behind the competition and even behind Apple's iPhone 11 Pro models
- The included power adapter is inadequate
The Ugly
- The screen is unimpressive, with a low resolution and relatively poor contrast (color accuracy is good, though)
https://arstechnica.com/gadgets/2019/09/iphone-11-review-the-sweet-spot-iphone/
2019-09-29 12:00:00Z
52780396660096